#SQL injection dork
Explore tagged Tumblr posts
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌𝚞𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜𝚎𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
Ethical Hacker Course: Key Skills You Will Learn
With the increasing number of cyber threats and data breaches worldwide, the demand for skilled ethical hackers is higher than ever since the past two decades. An ethical hacker course equips professionals with the knowledge and hands-on experience needed to identify, exploit, and fix the security vulnerabilities in networks & systems. If you are looking for career in cyber security, here’s a very depth analysis at the important skills you will learn in an ethical hacking course.
Core Modules in an Ethical Hacker Course
An ethical hacking course covers various modules designed to provide a solid foundation in cybersecurity. Some of the core modules include:
1. Introduction to Basics of Ethical Hacking
Understanding the role & responsibilities of an ethical hacker
Legal & ethical considerations in cybersecurity
Different types of cyber threats and attack methodologies
2. Footprinting and Reconnaissance
Gathering information about a target system using open-source intelligence (OSINT)
Using tools like Nmap, Maltego, and Google Dorking to identify vulnerabilities
Techniques such as passive and active reconnaissance
3. Scanning Networks and System Hacking
Identifying open ports, services, and vulnerabilities
Exploiting security loopholes using vulnerability scanners
Password cracking techniques, privilege escalation, and maintaining access
4. Malware Threats & Attack Vectors
Understanding types of malware: viruses, worms, ransomware, and trojans
Analyzing malware behavior & prevention strategies
Using sandboxing & endpoint protection tools
5. Web Application Security
Detecting common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF)
Security testing methodologies for web applications
Understanding Secure Software Development Life Cycle (SDLC)
6. Wireless Network Security
Understanding Wi-Fi encryption standards (WEP, WPA, WPA2, WPA3)
Conducting wireless penetration testing
Preventing wireless network intrusions
7. Cryptography and Network Security
Basics of encryption, hashing, and digital signatures
Implementing secure communication channels
Understanding of VPNs, firewalls and Intrusion Detection Systems (IDS)
Hands-On Learning: Practical Exercises and Real-World Scenarios
Ethical hacking courses emphasize hands-on learning to prepare professionals for real-world cybersecurity challenges. Some key practical aspects include:
Penetration Testing Labs: Simulated environments where students can practice exploiting vulnerabilities.
Capture The Flag (CTF) Challenges: Gamified cybersecurity competitions to test hacking skills.
Incident Response Simulations: Handling real-world cybersecurity incidents, including data breaches and denial-of-service (DoS) attacks.
Reverse Engineering and Exploit Development: Analyzing malicious code and writing exploits for vulnerabilities.
By working on real-world cybersecurity scenarios, ethical hackers develop real time problem solving skills and learn to think like attackers to defend systems very effectively.
Important Tools & Tactics Used by Ethical Hackers
Ethical hackers used the various tools and techniques to perform security assessments. Some of the essential tools include:
Kali Linux: A penetration testing operating system with a wide range of security tools.
Metasploit Framework: A very powerful tools for developing and executing exploit any code.
Burp Suite: A web vulnerability scanner used for security testing of web applications.
Wireshark: A network protocol analyzer for capturing & analyzing network traffic in the systems.
John the Ripper and Hashcat: Password cracking tools.
Nmap and Zenmap: Network scanning tools for identifying vulnerabilities.
SQLmap: A tool that used for detecting & exploiting My SQL injection vulnerabilities.
Using these tools, ethical hackers perform penetration testing, vulnerability assessments, and forensic analysis to strengthen an organization’s security posture.
Complement Certifications CEH for Career & Growth:
While the Certified Ethical Hacker certification is a highly demanding credential, comparing it with other certifications can further improve your career opportunities. Some of the complementary certifications include:
1. Offensive Security Certified Professional (OSCP)
Focuses & Improve on hands-on penetration testing skills.
Requires candidates to complete a challenging 24-hour practical exam.
Those who are looking to specialize in offensive security.
2. GIAC Penetration Tester (GPEN)
Covers advanced penetration testing techniques.
Recognized by government and enterprise cybersecurity teams.
Focuses on exploit development, privilege escalation, and password attacks.
3. Certified Information Systems Security Professional (CISSP)
Covers broad cybersecurity domains, including risk management and governance.
Ideal for those aspiring to take on security management roles.
Highly valued by employers worldwide.
4. CompTIA PenTest+
Covers penetration testing methodologies, tools, and reporting.
A good alternative for those starting in ethical hacking.
5. EC-Council Certified Security Analyst (ECSA)
Advanced ethical hacking certification that builds on CEH.
Covers in-depth penetration testing methodologies.
Ideal for professionals looking to specialize in vulnerability assessment and red teaming.
Conclusion
An ethical hacker course provides professionals with in-depth knowledge and hands-on experience in cyber security programs. From network scanning and malware analysis to penetration testing and web security, ethical hackers develop a very powerful skill set to protect organizations from cyber threats. With the right combination of certifications and in depth practice, ethical hackers can advance their careers and contribute to strengthening global cyber security defenses. Are you ready to take on your ethical hacking journey? Start learning today and build a rewarding career in cybersecurity!
#ceh certification requirements#ethical hacking course#hacking course#ethical hacking courses#ethical hacker course
0 notes
Text
BigBountyRecon sử dụng 58 kỹ thuật khác nhau bằng cách sử dụng các công cụ mã nguồn mở và dorks khác nhau của Google để đẩy nhanh quá trình do thám mục tiêu. Trinh sát là bước quan trọng nhất trong bất kỳ thử nghiệm thâm nhập hoặc quy trình săn lỗi nào. Nó cung cấp cho kẻ tấn công một số thông tin sơ bộ về mục tiêu. Hơn nữa, sẽ rất hữu ích khi hiểu rõ những biện pháp bảo vệ nào đang được áp dụng cũng như một số ước tính sơ bộ về mức độ bảo mật của mục tiêu. Công cụ này có thể được sử dụng để săn lỗi. Ý tưởng của công cụ này là nhanh chóng kiểm tra và thu thập thông tin về mục tiêu của bạn mà không cần đầu tư thời gian và ghi nhớ các tác vụ này. Ngoài ra, nó có thể giúp bạn xác định một số cách tiếp cận để nhanh chóng khai thác mục tiêu. Kỹ thuật mà BigBountyRecon sử dụng BigBountyRecon có tới 58 kỹ thuật khác nhau, nhưng để tiết kiệm thời gian thì mình chỉ giới thiệu 10 kỹ thuật mà mình thấy ấn tượng cũng như được sử dụng nhiều nhất dưới đây: 1. Danh sách thư mục: Tìm các thư mục mở bằng Google Dork trên mục tiêu giúp bạn hiểu cấu trúc thư mục trên máy chủ web. Nó có thể làm lộ thông tin nhạy cảm hoặc có thể dẫn đến lộ thông tin. 2. Tệp cấu hình: Thông thường, tệp cấu hình chứa thông tin nhạy cảm như mật khẩu được mã hóa cứng, vị trí ổ đĩa nhạy cảm hoặc key API có thể giúp bạn có được quyền truy cập đặc quyền vào tài nguyên nội bộ. 3. Tệp cơ sở dữ liệu: Tệp cơ sở dữ liệu là tệp dữ liệu được sử dụng để lưu trữ nội dung của cơ sở dữ liệu ở định dạng các bảng và trường riêng biệt. Tùy thuộc vào bản chất của ứng dụng web, các tệp này có thể cung cấp quyền truy cập vào thông tin nhạy cảm. 4. WordPress: WordPress là một CMS mã nguồn mở được viết bằng PHP. WordPress có hàng nghìn plugin để xây dựng, tùy chỉnh và nâng cao các trang web. Nhưng cũng có rất nhiều lỗ hổng trong các plugin này. 5. Tệp nhật ký: Các tệp nhật ký đôi khi cung cấp thông tin chi tiết về hoạt động của người dùng trong một ứng dụng cụ thể. Các tệp này thường được dùng để xem cookie phiên hoặc các loại mã thông báo kh��c. 6. Tệp sao lưu và tệp cũ: Các tệp sao lưu là bản sao gốc của các hệ thống quan trọng. Chúng cung cấp quyền truy cập vào PII hoặc quyền truy cập vào các hồ sơ nhạy cảm. 7. Trang đăng nhập: Điều cực kỳ quan trọng là xác định các trang đăng nhập của mục tiêu của bạn để thực hiện bruteforce hoặc thử thông tin đăng nhập mặc định để có thêm quyền truy cập vào các tài nguyên của tổ chức. 8. Lỗi SQL: Lỗi SQL làm rò rỉ thông tin nhạy cảm về hệ thống phụ trợ. Điều này có thể giúp bạn liệt kê các loại cơ sở dữ liệu và xem liệu ứng dụng có dễ bị tấn công bằng lỗi liên quan đến xác thực đầu vào như SQL Injection hay không. 9. Tệp cấu hình Apache: Máy chủ Apache HTTP được cấu hình bằng cách đặt các chỉ thị trong tệp cấu hình văn bản thuần. Tệp cấu hình chính thường là httpd.conf. Tùy thuộc vào các mục nhập trong các tệp cấu hình này, nó có thể tiết lộ các chuỗi kết nối cơ sở dữ liệu, tên người dùng và mật khẩu, hoạt động bên trong, các thư viện được sử dụng và tham chiếu cũng như logic của ứng dụng. 10. Tệp Robots.txt: Tệp Robots.txt hướng dẫn robot web cách thu thập dữ liệu trên trang web của chúng. Tùy thuộc vào nội dung của tệp, kẻ tấn công có thể phát hiện ra các thư mục và tệp ẩn. Ngoài ra, còn có thêm 48 kỹ thuật khác mà bạn có thể tìm hiểu tại đây. Cách sử dụng BigBountyRecon Bước 1: Đầu tiên các bạn tải công cụng BigBountyRecon tại đây. Bước 2: Tiếp theo các bạn cần mở file EXE vừa mới tải về. Bước 3: Nhập tên miền của mục tiêu. Bước 4: Nhấp vào các nút khác nhau trong công cụ để tìm thông tin. Bước 5: Trong trường hợp gặp Google Captcha, bạn chỉ cần xác thực và tiếp tục.
0 notes
Link
Do you want to know how to find admin panel of website and how to bypass website admin panel ? If your answer is yes, then you have to check this link.
1 note
·
View note
Text
Cross Site Request Forgery
Cross Site Request Forgery
Cross Site Request Forgery
After a long time I came up with a tutorial of hacking. Now the name of the hacking will be shown as XSS or Cross Site Scripting. In this tutorial, I hope you will try to teach on this method altogether. KaliLinuxExpert said the hacking class will arrange the class. But TJ mint leaves have not started yet due to lack of time. So sometimes you write something for…
View On WordPress
#Cross Site Request Forgery#cross site scripting#dom based xss#google dork#Google dorks list#Google hacking commands#How to hack google data base#How to prevent cross site scripting#SQL Injection#SQL injection course#xss cheat sheet
1 note
·
View note
Text
Fawkes - Search For Targets Vulnerable To SQL Injection
Fawkes - Search For Targets Vulnerable To SQL Injection #Engine #Fawkes #Google #GoogleSearch #injection #Performs
Fawkes is a tool to search for targets vulnerable to SQL Injection. Performs the search using Google search engine. Options -q, --query - Dork that will be used in the search engine. -r, --results - Number of results brought by the search engine. -s, --start-page - Home page of search results. -t, --timeout - Timeout of requests. -v, --verbose - Enable verbosity. Examples: python3 fawkes.py…
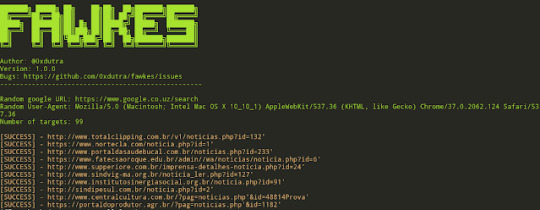
View On WordPress
#Engine#Fawkes#Google#Google Search#injection#Performs#python#python3#Search#sql#SQL Injection#Targets#tool#Vulnerable
1 note
·
View note
Text
Hack Forum Yazım ve Ben
Hack Forum internet siterinden bahsedeceğim blog yazıma hoş geldiniz. Öncelikle kendimden kısaca bahsetmem gerekirse; Adım İhsan Bayuncuk 27 yaşındayım ve 11 yıldır hackerım. Hack yapmaya başladığımda 16 yaşındaydım. ilk olarak Wordpress tabanlı siteleri brute force yöntemi ile hackliyordum. Hacking işleminin ardından siteyi önce kopyalayıp sonra deface ediyordum. Kopyalama işlemi yaptığım internet sitelerinin yedeklerini, önce moderatör veya adminlere danışarak üyesi olduğum hack forum sitesinde paylaşıyordum. Bazen site sahipleri gelip kaldırmama yada ona verdikten sonra kaldırmamı istiyordu. Ben bunun için para teklif ediyordum ancak çok azı kabul ediyordu. Parayı kendi adıma alıyordum ancak şans eseri başıma hack yüzünden hiç bela gelmedi. Ardından daha gelişmiş bir hacking yöntemine geçtim, hangi yöntem mi ? Tabikide SQL açıkları. Öncelikle cihazıma Linux işletim sisteminin kali dağıtımını kurdum ve içindeki SQLMap isimli hack tool programı çok işime yaradı. Google üzerinden dork yardımı ile buldum güvenlik açığı olan sitelere SQLMap ile sızıp deface ediyordum. Artık daha büyük ve değerli internet siteleri pençeme düştüğü gibi, aynı zamanda çokta pratik bir şekilde hacker faaliyetlerini yürütüyordum. Ben bu işi sevmiştim adamsın SQL. Yeni yöntemim olan SQL injection yöntemini üyesi olduğum hack forum sitesinden öğrenmiştim ve daha bir çok yöntem vardı hepsini öğrenmeye çalışıyordum. Ayrıca freelance olarak web tasarım işi yaptığım için warez temalarda bana zaman ve para kazandırıyordu.
2 notes
·
View notes
Photo

Google hacking, also named Google dorking, is a computer hacking technique that uses Google Search and other Google applications to find security holes in the configuration and computer code that websites use. Here are some Google dork queries
Google Dorks for hacking websites ==========================================
intitle: This dork will tell Google to show only those pages that have the term in their HTML title. For example: intitle:”login page” will show those pages which have the term “login page” in the title text.
allintitle: It is similar to intitle but looks for all the specified terms in the title. For example: allintitle:”login page”
google_ad_client = "ca-pub-8733588191385036"; google_ad_slot = "6223334052"; google_ad_width = 468; google_ad_height = 60;
inurl: It searches for the specified term in the URL. For example: inurl:”login.php” and inurl:proftpdpasswd
allinurl: It is similar to inurl but looks for all the specified terms in the URL. For example: allinurl:”login.php”.
define: Google will define this message and will look for what had this error. For example: define:”sql syntax error”
site: This dork will return all the pages of a particular website that is crawled by Google. For example, site:technotification.com.
link: It will also look in the site for URLs that possibly are vulnerable to sql injection. For example: link:index.php?id= Google Dorks for hacking files ====================================================
filetype: Searches for specific file types. filetype:pdf will look for pdf files in websites. filetype:txt looks for files with .txt extension. This way you can search for a file with any extension like mp4, mp3, Mkv, etc. site:onedrive.live.com shared by
intitle: You can look into file directories of websites directly and download specified file intitle: index of mp3 for mp3 files. You can replace mp3 with any other extension. You can also use to find any particular movie or game. intitle: “index of ” intext: “movie name” .
book: find any book using Google search engine. for example: book: java Google Dorks for finding username and passwords ===================================================
intext: passwords filetype: txt
mysql history files
intext: account details filetype: txt
intitle:index.of intext:”secring .skr”|&q…
people.lst
passwd
master.passwd
pwd.db
htpasswd / htpasswd.bak
htpasswd / htgroup
spwd.db / passwd
passwd / etc (reliable)
config.php
passlist
3 notes
·
View notes
Text
TSP Dork generator v11.0 New 2019
Link download: http://www.mediafire.com/folder/s2zkwscubbfbq/TSP_Dork_generator pass-222 Please visit My Blog : share-cracked-tools.tumblr.com YouTube Channel For SQL Injection : https://www.youtube.com/channel/UCIcRvNfJYQ2w-J5yc-AvJdw https://www.youtube.com/channel/UCcIwZ-NliCPovnQv8rpd1vA
2 notes
·
View notes
Text
[Media] SQLI Dorks Generator
SQLI Dorks Generator This is simple script for generate dorks list for sql injection https://github.com/Zold1/sqli-dorks-generator #sql #dork

0 notes
Text
SQLiv – SQL Injection Dork Scanning Tool
http://i.securitythinkingcap.com/Px9JYb #PenTest
1 note
·
View note
Photo

New Google Dorks List Collection for SQL Injection – SQL Dorks 2019
0 notes
Text
SQLiv - Massive SQL Injection Vulnerability Scanner
SQLiv - Massive SQL Injection Vulnerability Scanner #Vulnerability #Injection #SQL #SQLI #Hacking #Scanner #python #infosec
Massive SQL injection vulnerability scanner.
Features
multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo
targetted scanning by providing specific domain (with crawling)
reverse domain scanning
both SQLi scanning and domain info checking are done in multiprocessing so the script is super fast at scanning many urls
quick tutorial & screenshots are shown at the bottom project…
View On WordPress
#dorks#google dorks#Injection Vulnerability Scanner#linux#mac#Massive#Scanner#sql#SQL Injection#SQL injection dork#SQL Injection Vulnerability Scanner#SQLi#SQLiv#Vulnerability#Vulnerability Scanner
0 notes
Text
All in One Video Downloader 1.2 - SQL Injection

# Exploit Title: All in One Video Downloader 1.2 - SQL Injection # Google Dork: "developed by Niche Office" # Date: 1 Jan 2019 # Exploit Author: Deyaa Muhammad # Author EMail: contact [at] deyaa.me # Author Blog: http://deyaa.me # Vendor Homepage: https://nicheoffice.web.tr/ # Software Link: https://codecanyon.net/item/all-in-one-video-downloader-youtube-and-more/22599418 # Demo Website: https://aiovideodl.ml/ # Demo Admin Panel: https://aiovideodl.ml/admin/ # Demo Admin Credentials: [email protected]/123456 # Version: 1.2 # Tested on: WIN7_x68/cloudflare # CVE : N/A
# POC: https://[PATH]/admin/?view=page-edit&id=2.9'+[SQLI]-- -
# Exploit: https://[PATH]/admin/?view=page-edit&id=2.9'+UNION+SELECT+1,2,3,4,concat(user(),0x3a3a,database(),0x3a3a,version())-- -
#Live Target: https://aiovideodl.ml/admin/?view=page-edit&id=2.9'+UNION+SELECT+1,2,3,4,concat(user(),0x3a3a,database(),0x3a3a,version())-- -
# References: https://packetstormsecurity.com/files/150955/All-In-One-Video-Downloader-1.2-SQL-Injection.html
0 notes
Text
SaltOS Erp Crm 3.1 r8126 - SQL Injection (2)
Exploit Title: SaltOS Erp, Crm 3.1 r8126 - SQL Injection # Dork ... Gecko/20100101 Firefox/55.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: tr-TR,tr;q=0.8, ... from crm application - BingNews https://ift.tt/2zclfGC https://ift.tt/eA8V8J October 29, 2018 at 12:31PM
0 notes